Yahoo! – and to a lesser extent Hotmail – were the kings of the Internet in the late 1990s. Their free webmail services gave anyone with a modem a digital identity. But this openness had a fatal flaw: it was built on trust.

By 1999, this trust was exploited by the first generation of spam bots.
The crisis revealed how vulnerable the Internet really is. An enthusiastic teenager with a basic understanding of Python can write a simple script that can interact with websites directly. These programs didn’t need to understand the nuances of the Internet. They just needed to realize that when they encountered an HTML field called “email_address,” they had to enter a string of random characters, and when they saw a button called “Submit,” they had to simulate a click.
These scripts turned the Internet into a playground for what became known as “script kids”: people who used pre-written code to wreak havoc without really understanding how it worked. The texts were “headless,” meaning they didn’t need to load images or design that a human might see. They worked on the raw text skeletons of websites, moving at the speed of a processor. Where it might take a human two minutes to navigate a subscription flow, a basic script can execute the same sequence in milliseconds.
By the time Yahoo! Hotmail realized they had a problem: millions of fake accounts were being created by just a few computers running frequently.
This early automation was the primitive soup of the modern botnet.
Direct attempts to monitor and trace the origins of spam bots quickly became extremely impractical. Another solution must be found.
It was a team at Carnegie Mellon University, led by 21-year-old Louis von Ahn, that came up with an answer in 2000: what came to be called the Completely Automated Public Turing Test for Distinguishing Computers from Humans, or CAPTCHA.
The concept was elegant in its cynicism. The machine will rule over humanity. By displaying distorted text that could be read by humans through pattern recognition, but was baffling to optical character recognition software at the time, the team built a digital portal.
It worked for a few years. But as with any technological solution, the arms race had only just begun.
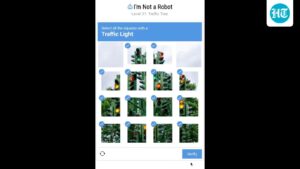
The next iteration, reCAPTCHA (also invented by von Ahn, in 2007), introduced familiar image grids, asking users to identify fire hydrants, bicycles, or traffic lights. It was clever social engineering.
While users thought they were simply proving their status as humans in order to gain access to a website, they were also providing free labor, and the massive datasets required to train the next generation of AI. AI has learned from all of us what a cycle looks like. Every crossing we identified helped teach self-driving cars how to see the world.
***
In 2018, a fundamental shift occurred. Google, which acquired CAPTCHA from Carnegie Mellon University in September 2009, launched reCAPTCHA v3. Instead of interrupting users with challenges, this version runs almost entirely in the background. Using a JavaScript application programming interface (or application programming interface), it assigns each interaction a score between 0.0 and 1.0, indicating how likely it is to be a bot (with 1.0 being highly likely the user is a human).
It became a system of constant, invisible surveillance, judging users not by their ability to solve the puzzle, but by the chaos of their mouse movements and the unpredictable rhythm of their scrolling.
This move brought new problems. When the system couldn’t see the “messy” data it expected from ordinary users, it resorted to suspicion. Power users navigating with super-fast keyboard shortcuts, or those using privacy-focused browsers that block tracking scripts, have started triggering false positives for bot activity. Users found themselves trapped in endless “please try again” loops, or banned entirely from services without explanation.
This shift has created particular challenges with regard to accessibility. As with traditional CAPTCHA, reCAPTCHA v3 has become a barrier for differently abled and assistive device users. Platforms began offering backup authentication options like email codes and voice challenges, but these reintroduced the very friction the systems were trying to eliminate.
***
Beneath these apparent problems has been a quiet shift in how identity itself is inferred online.
Modern bot detection increasingly relies on device fingerprinting: the collection of dozens or hundreds of small signals about a user’s environment. Screen resolution, installed fonts, GPU characteristics, sound stack behavior, clock skew, and network patterns, none of these are determined on their own, but together they form a probabilistic silhouette of the device.
This fingerprint is difficult to convincingly fake.
It is also difficult to escape.
Users who take deliberate steps to protect their privacy, by disabling JavaScript, randomizing user agents, blocking trackers, or routing traffic through virtual private networks or VPNs, often end up with statistically rare fingerprints. In systems trained to detect anomalies, scarcity itself is suspect.
This creates a reflection of early Internet values. Whereas anonymity was previously a default, it is now treated as a sign of a potential threat. The more ambiguous one chooses to be, the more friction one can expect to encounter. Trust is no longer given by credentials alone, but by conformity to the expected pattern.
While it is still true that the gatekeeper does not need to know who you are; She just needs to know that you act like others she’s seen before… In order for her to meet that standard, well, you need to tell her at least a little bit about who you are.
***
At the same time, robots are becoming faster, cheaper and smarter. Sophisticated software can simulate human clicks and even solve basic picture puzzles using artificial intelligence.
With AI now becoming a tool on both sides, the battle is shifting to a higher level.
Instead of trying to outmaneuver bots, algorithms created by companies like Arkose Labs flip the script — simply by giving them more to do.
In the world of high-stakes cybercrime, ROI is the only metric that matters. If orchestrating an attack costs more electricity and server time than data, the attacker will simply walk away.
So modern proof-of-work systems force the visitor’s computer to solve complex mathematical puzzles in the background. For a legitimate human user with a modern device, the task is a simple image in the background. But for a botnet trying millions of simultaneous logins, this becomes very expensive.
In this strategy of deliberate inefficiency, the system allows the botnet to get rid of CPU cycles and electricity. By the time she gives her answers, she has already revealed her mechanical nature through her persistence. The gate guard wouldn’t let him in.
This may be the battle won, but it will not be the end of the war.
We have reached the point where artificial intelligence can behave so much like us that we have to invent increasingly sophisticated ways to prove that we are not like them. As we use AI to automate more basic online interactions, we risk removing the accessible entry points that previously allowed everyone to participate.
Meanwhile, the gatekeepers are invisible, the tests are behavioral, and there is a cost of entry It is a constant stream of data about how we move and think. In our efforts to keep robots at bay, we have created a system that requires us to be monitored, tracked, and assigned tasks invisibly, simply to prove that we are human.
The question now is not whether we can stay ahead of robotics. Like the Red Queen in Lewis Carroll’s Alice, it’s a matter of how fast you can run, just to stay in the same place.
Except it’s not the same place, right? We no longer really have the openness and anonymity that made the Internet so revolutionary in the beginning.
(K Narayanan writes about movies, video games, books, and sometimes technology)